Restructuring Status Report
Overview
Organizations always need to enhance their security through network protection. They must hire people with the right skills or train the team in charge of protecting the network. Companies can grow or downsize rapidly, and their network configurations need to adapt just as quickly. A strong traffic flow policy will help the company manage these changes. The focus of this project is creating a traffic flow policy that includes firewall rules.
As a cybersecurity analyst, you must develop different forms of technical expertise, including the ability to complete discrete tasks. The ability to take a holistic view of security and be mindful of the global effects of configurations on a system is equally important. This expertise will help you better understand an organization’s security posture as a whole.
For this project, you will use the virtual sandbox to create a proof of concept for the upcoming organizational restructuring.
The project incorporates one milestone, which will be submitted in Module Five. Use instructor feedback on your pre-planning milestone to reconfigure the network in your lab this week. The project will be submitted in Module Seven.
In this assignment, you will demonstrate your mastery of the following competency:
- Implement a traffic flow policy based on organizational security strategy
Scenario
Congratulations! You got the job! You are a cybersecurity analyst with a company that is restructuring. Your manager has asked you to use the virtual sandbox from your interview to create a proof of concept of a network configuration that reflects the new organizational structure. Use the network reconfiguration plan you already created to develop a restructuring status report that documents your technical work and thoughts on how this work improves the organization’s overall security posture.
Prompt
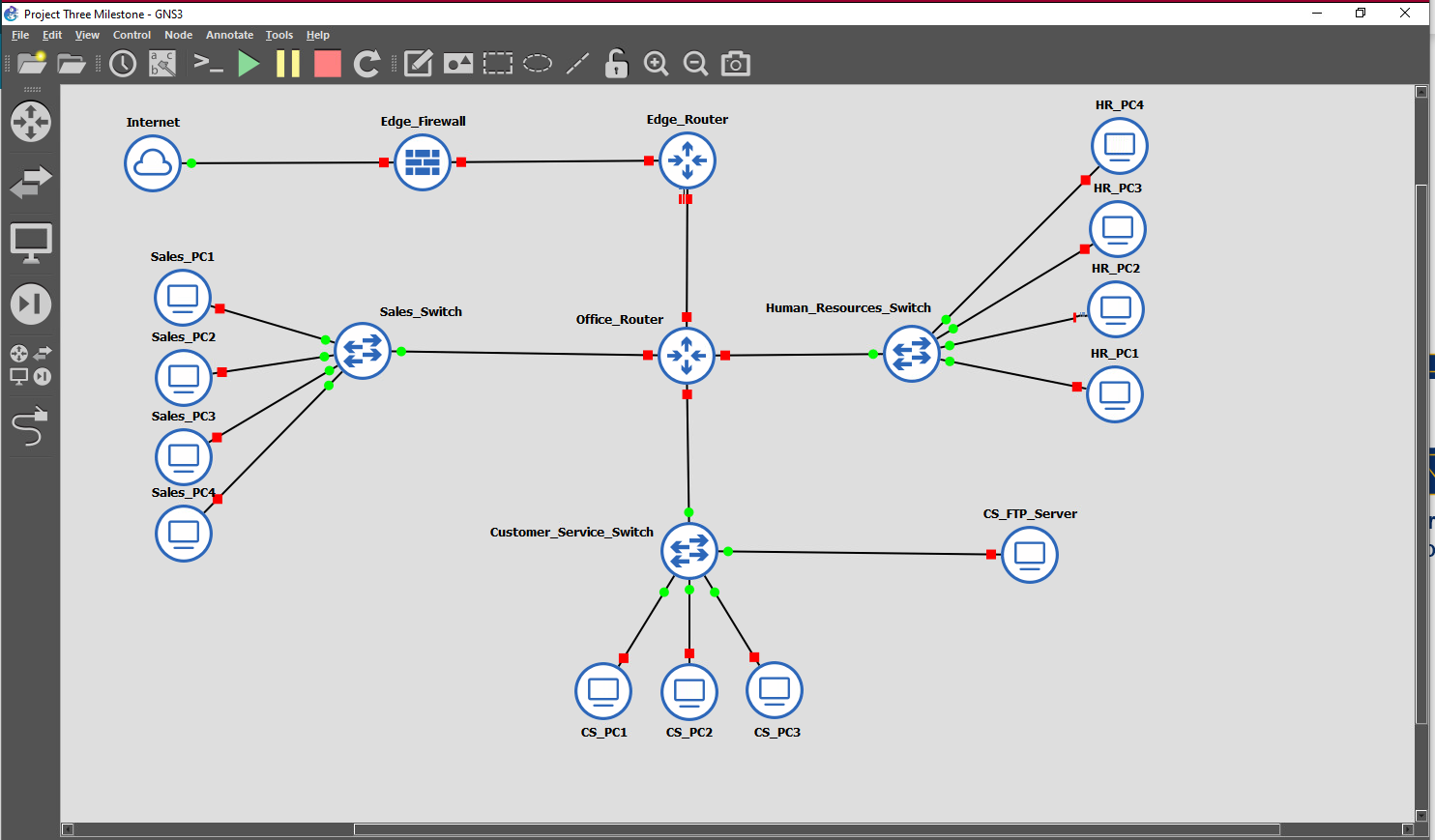
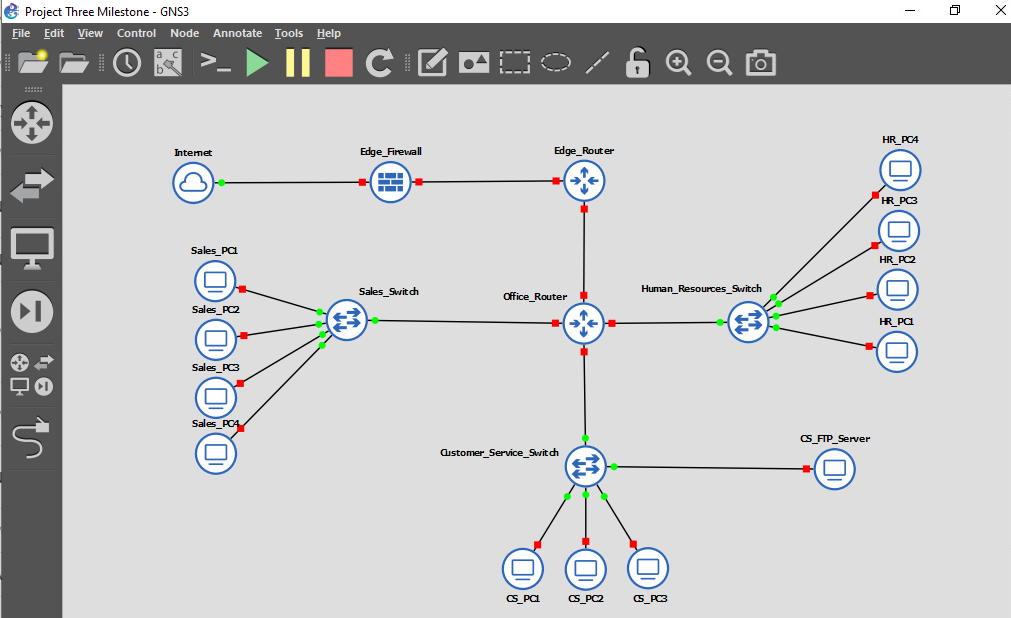
Open the CYB 310 Sandbox, click on the GNS3 icon, and select Project Three from the Projects Library list. Note: You must complete this project in one sitting, as the lab environment is non-persistent. Be aware of your time as you complete the lab. You can extend your lab when the time warning appears.
You must address the following rubric criteria:
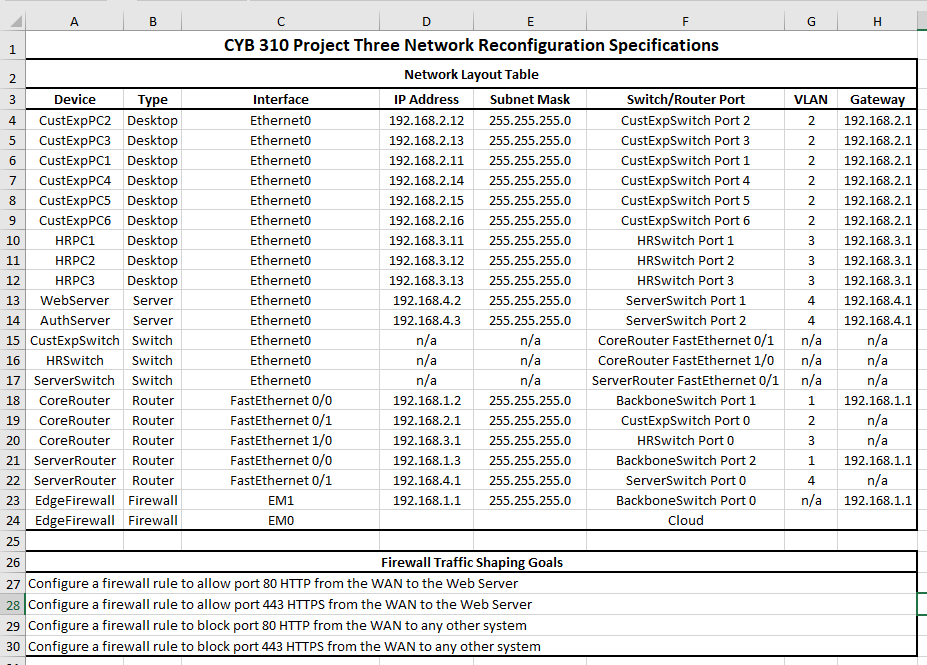
- Network Reconfiguration: Include the following screenshots:
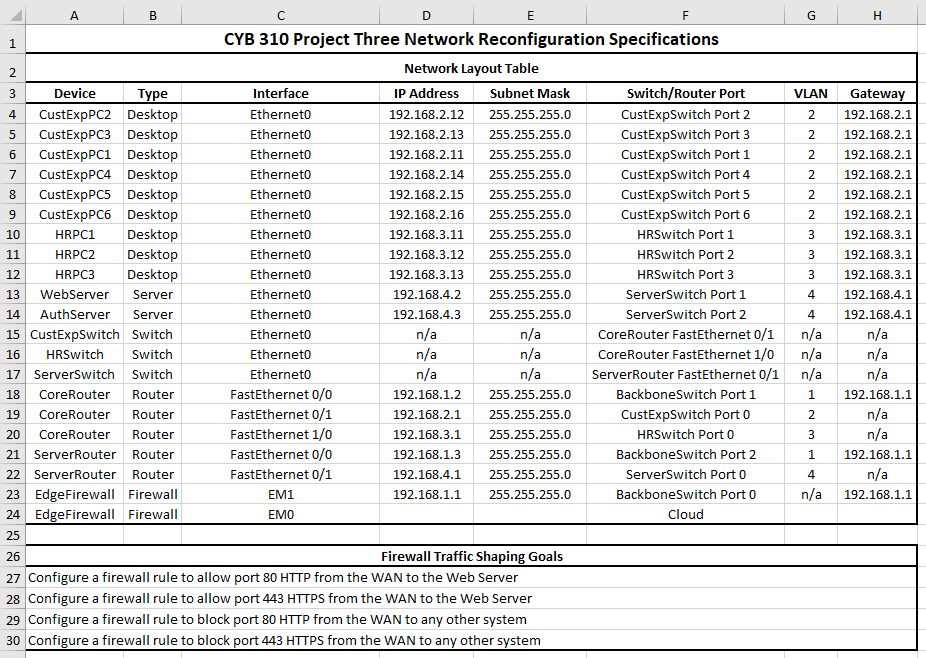
- Network diagram
- Port assignment and VLAN assignment for each switch
- Traffic Flow Configuration: Include screenshots of the following:
- Configure a firewall rule to allow port 80 HTTP from the WAN to the FTP server.
- Configure a firewall rule to allow port 443 HTTPS from the WAN to the FTP server.
- Configure a firewall rule to block port 80 HTTP from the WAN to any other system.
- Configure a firewall rule to block port 443 HTTPS from the WAN to any other system.
- Organizational Security Strategy
- Explain how the security posture of the organization has been improved by the restructuring.
- Describe how the tenets of the CIA triad (confidentiality, integrity, and availability) are affected by the restructuring.
Project Three Network Reconfiguration Specifications Spreadsheet
Project Three Milestone - GNS3